Challenge 08 is more of a real-world challenge than some of the others have been. It’s also very dear to my heart, getting back to my networking roots.
You are instructed simply to check out what the level08 user has been up to. This is fairly easy, since when you login as level08, you see a “capture.pcap” file in their home folder. A pcap file is a standard packet capture file format. More details can be found here.
If you open this file in WireShark, a popular network monitoring program, you can see that a tcp stream was recorded. You can also see the plain-text “conversation” between both hosts, by right-clicking on one of the packets, and clicking, “Follow TCP Stream”.
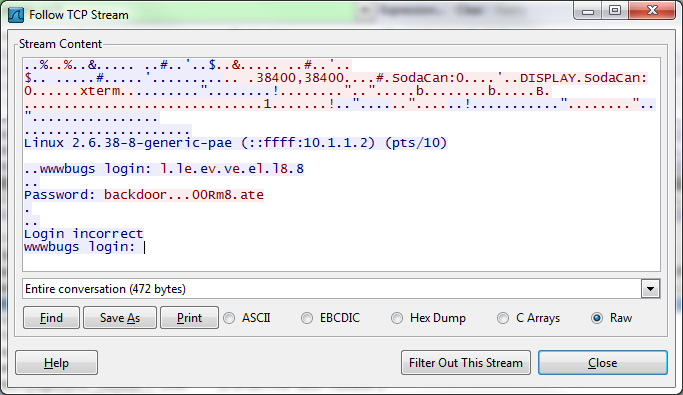
For a while, I thought this was the end of this problem, however it bugged me a bit, that the challenge instructions said, “and use it to log into flag08 account”. So I went digging some more.
I decided that since I could not login to flag08 as “backdoor…00Rm8.ate”, I would re-analyze the file. I this time, looked at it in hex, and saw that the periods were actually a representation of the 0x7f digit:
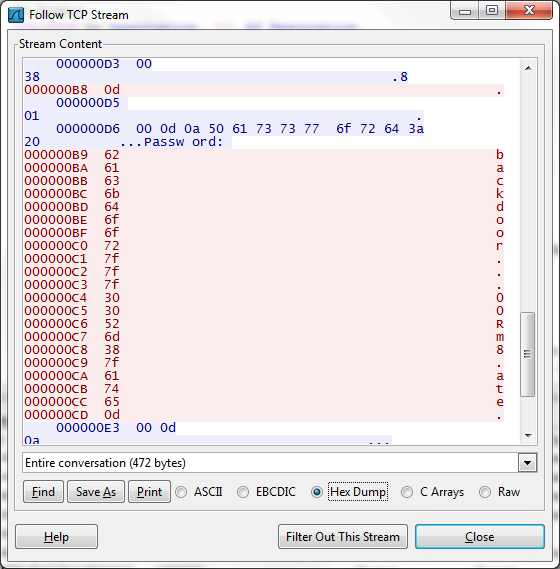
Now I’m familiar with a lot of hex digits without having to look them up, since I tinker with exploit development, and have been coding random languages for 15 years or so. However, I had not remembered ever seeing 0x7f. I looked it up on an ASCII table and found that it was actually the key code for “Delete”. So it looks like the flag08 user had some issues remembering their password, and had to delete some of the typed keys and re-type them. If you pretend to type the password from the “capture.pcap” file, including the delete keys (use backspace), you end up with the password of “backd00Rmate”.
To test this, we can simply use su. Once it works, run “getflag” to complete the challenge.
level08@nebula:/home/flag08$ su flag08
Password:
sh-4.2$ getflag
You have successfully executed getflag on a target account






