I’m a customer of Hover for my domain name needs. However, that will be changing because I don’t believe that they take issues seriously.
The first security issue
I was browsing their site, looking for a new domain, and being the constant tinkerer I am, I entered a single quote into the textfield. I noticed an error, and eventually crafted this url:
https://www.hover.com/domains/results?q=%27%3E%3Cscript%3Ealert%28%27xss%27%29%3B%3C%2Fscript%3E
There’s nothing magical in that URL, however it demonstrated a real vulnerability in their code:
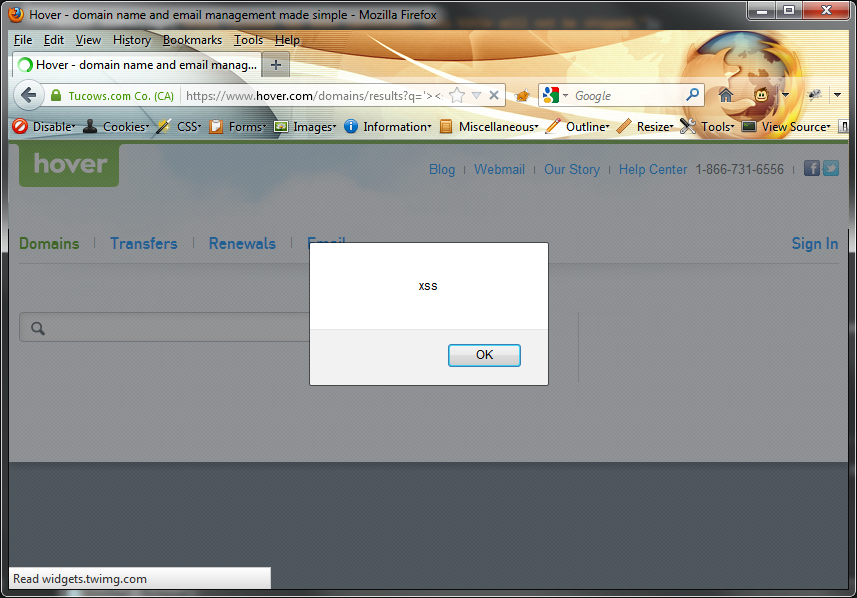
From that point, it could be trivial for an attacker to redirect traffic, and steal user sessions, thus being able to purchase domains with someone else’s money.
I reported this issue to them, and had an update within 3 days. They had fixed it, and that URL no longer is vulnerable.
The second security issue
In January, I was discussing Cross-Site Scripting attacks with a coworker, and was talking about the finding I had with Hover and how quickly they responded. Upon further investigation, I found that they didn’t really fix it, they just put a band-aid on it. I found the following URL was still vulnerable, but it was a little harder to exploit (onMouseOver):
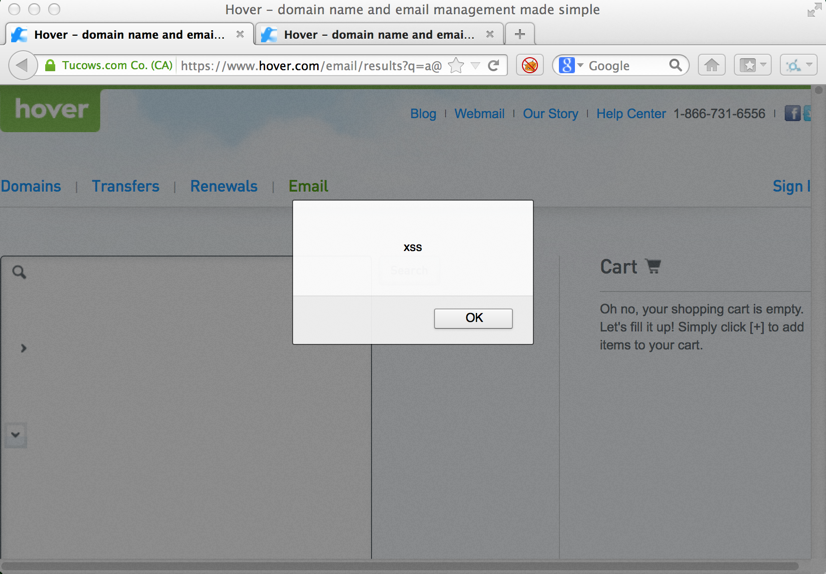
This really depressed me, since I have spent my fair share of time being a developer, and I always tried to actually fixproblems, instead of just making the symptom go away. Again, I reported the issue, hoping that I’d get another quick turnaround. I asked them to reply within 30 days to indicate their intent on coordinating efforts for remediation. I waited, but I still have no response from them, and it’s been over 30 days. I still can’t believe they couldn’t even respond with a, “We’re working on it”, response.
The billing issue
I received an email from Hover about a domain name of mine expiring soon. I went into my account, and saw that the credit card was expired, so I went to update it. Unfortunately, I got this error instead:
Declined by Fraud Service
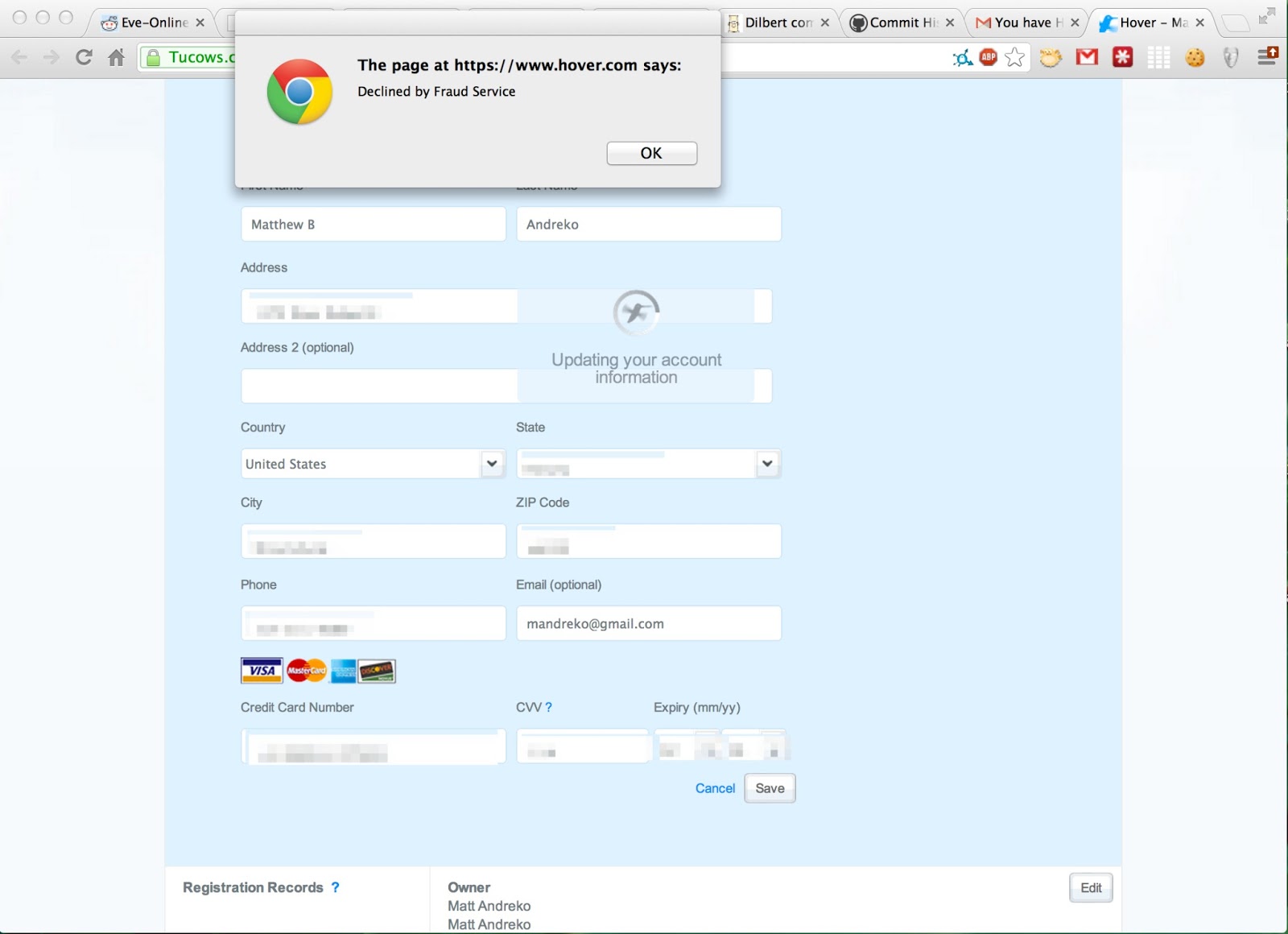
Now, I figured that it was some sort of error, and tried filling it out a couple more times, verifying my card number was correct.After-all, I was only updating the expiration date, nothing else. Unfortunately, all this resulted in were several temporary one dollar charges on my credit card.
Again, I contacted Hover and was disappointed yet again. I stated that I was trying to update my credit card details, and instead they renewed my domain for another year, and said, “it failed when you placed the order, but I was able to renew it on my end”. I was a bit upset because I hadn’t yet decided if I was going to renew through them or not yet, due to the previous security issues. I replied back that it still wasn’t helping me for my other domains that will need renewed at some point, and was given these instructions to help troubleshoot:
- Use only the first and last name, no middle initial.
- Change the phone number to numbers only, no hyphens.
The first one was a bit odd, since most credit card processors want your name exactlyas it shows on the card. I complied, but it did not help. The second issue I thought was absurd because if their system didn’t allow hyphens, why didn’t they prevent the user from entering them? This is exactly what javascript validation is for. (Note that they should also validate it on the server-side as well)
Their next steps were to have me call, and give them my credit card number over the phone, and have a billing statement ready to verify every bit of information, as if I’ve never used a credit card on a website before. It was a bit insulting.
The 0-day security issue
I had recently read an article on inserting javascript into DNS to be used for exploitation. I was tinkering with this idea on my own domain names. Unfortunately, I ended up trying to diagnose why none of the DNS records I created in Hover’s DNS Manager ever made it to their public DNS servers. I’m guessing they have some filtering on the back-end. Eventually I found that their DNS manager was also vulnerable to Cross-Site Scripting:
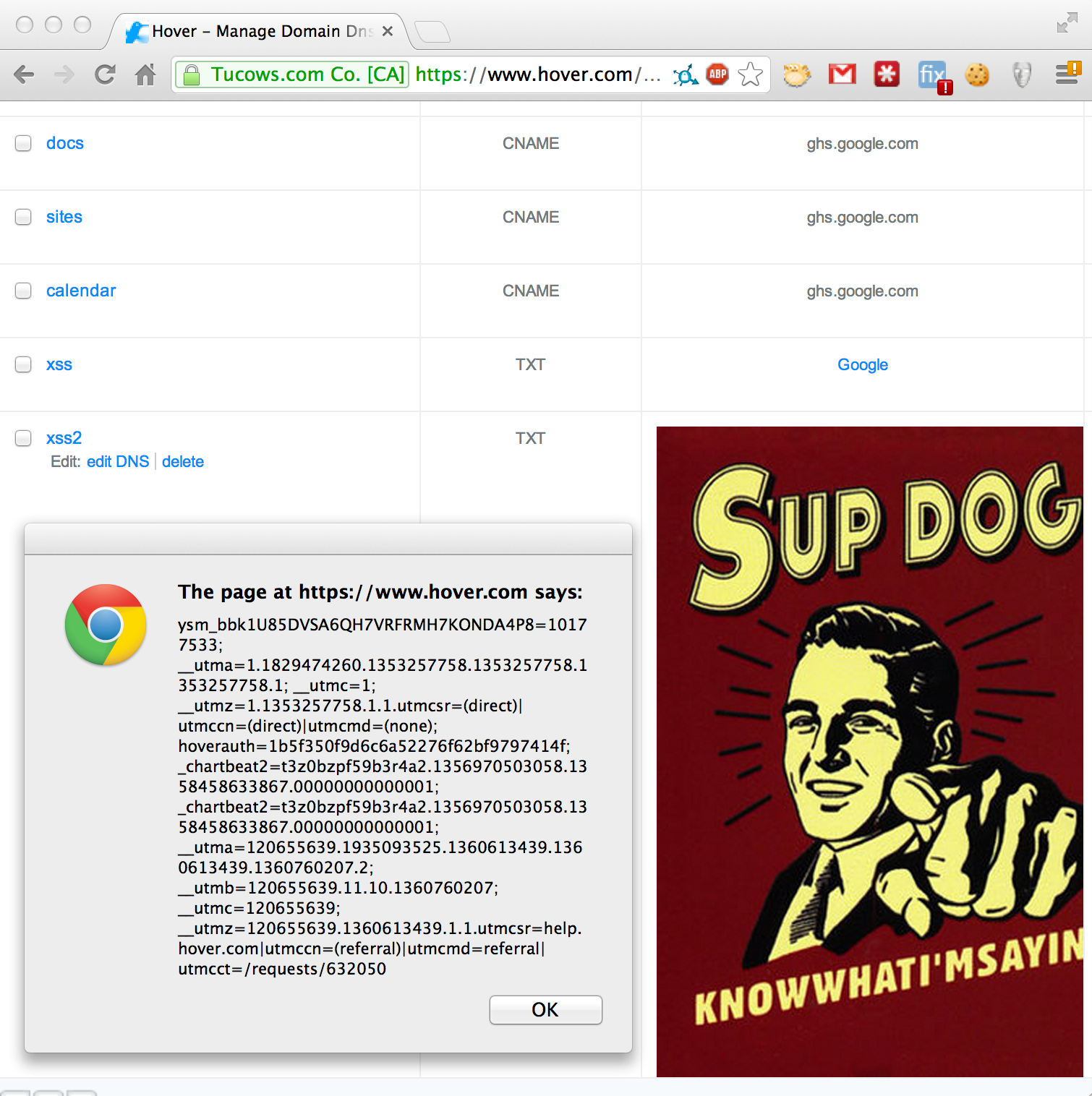
This time, it’s a persistent Cross-Site Scripting vulnerability. Every time I navigate to my DNS management screen, I now get a dialog with my cookie. All a user had to do was add a TXT record with the following data:
<img src=‘https://drupal.org/files/images/sup-dog-magnet-c117515921.jpeg' onload=‘javascript:alert(document.cookie);’>
They apparently do not even try to filter user-input at all. It’s quite depressing.
Conclusion (tl;dr)
Hover seems to suffer from the inability to filter user-input. This has become a big problem over the last few years. There are many attacks stemming from this seemingly simple attack. I did my best, and tried reporting to them, but they seem unresponsive, and even when they are, it’s not always useful.
I will be moving my domains elsewhere. I haven’t yet decided where, and I have a bit of time, but I just don’t feel safe keeping my data stored somewhere that can’t even stop basic OWASP Top 10 vulnerabilities on their main page.






